GhostGate is a Single Packet Authorization (SPA) security solution designed for Linux servers, whose main objective is to reduce the attack surface by temporarily opening protected ports only on demand.
Anyone who manages servers knows the routine: a relentless barrage of noise in the logs. Brute-force attacks on the SSH port, automated vulnerability scans, a constant flow of unsolicited traffic reminding us that our services are perpetually exposed, waiting to be the next target. Traditional defense consists of building ever-higher walls: complex firewalls, intrusion detection systems, IP blocking tools. But what if the approach is wrong?
This is where GhostGate proposes a paradigm shift. It's not simply another firewall tool; it's a radically different security philosophy. Its fundamental principle is "security through invisibility." Instead of leaving a fortified door in plain sight, GhostGate ensures there is no visible door at all. Imagine a door that only materializes for those who know the secret incantation. To everyone else, there is only a smooth, impenetrable wall.
In this article, we won't just describe its features. We'll analyze the five most impactful and counterintuitive lessons we can learn from GhostGate's architecture—insights that could change the way you think about critical infrastructure defense.
1. Security Through Invisibility: The Magic of Knocking on a Locked Door
The traditional approach to securing a service like SSH is to leave port 22 open and rely on strong passwords, SSH keys, and tools like Fail2Ban. However, an open port is a magnet for attackers. It will always be subject to scans and brute-force attempts, generating noise and constant risk.
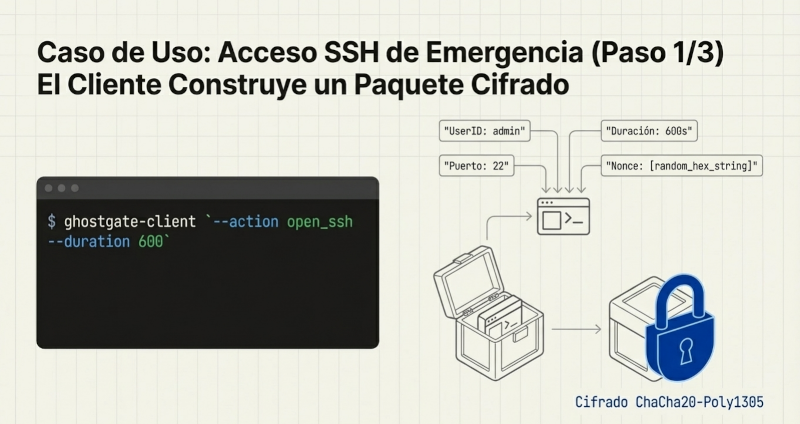
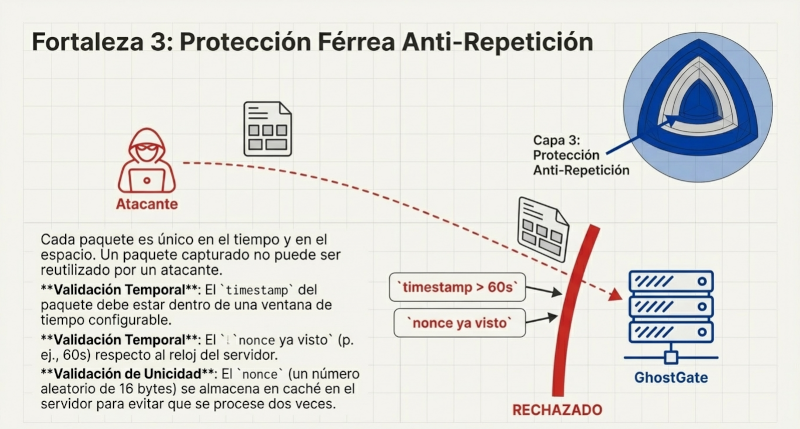
GhostGate reverses this model using Single Package Authorization (SPA). By default, the server firewall keeps all service ports, including port 22, completely closed. They are invisible to the outside world. When an authorized user needs access, they don't try to connect directly. Instead, they use a client such as ghostgate-client --action open_ssh --duration 600 to send a single UDP packet to a non-standard listening port. This packet, serialized in compact JSON format, is encrypted and authenticated using AEAD (Authenticated Encryption with Associated Data) encryption, acting as a "secret knock" on the wall.
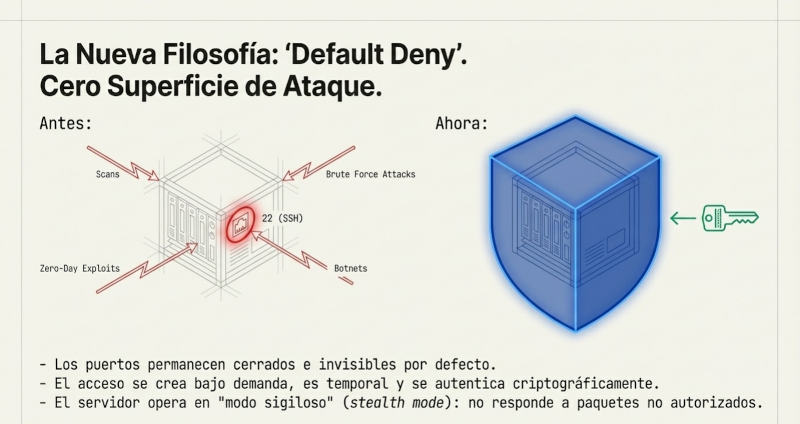
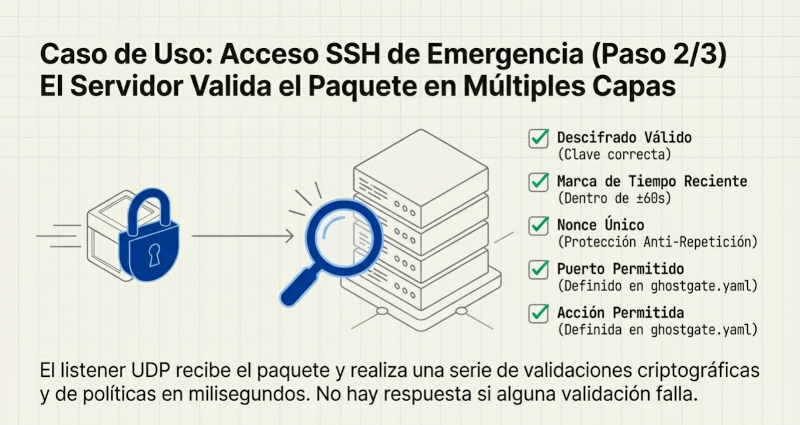
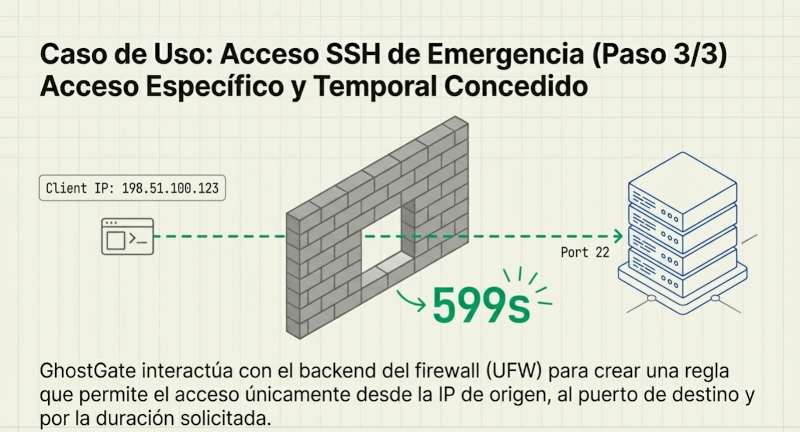
If the GhostGate listener receives this packet and verifies its authenticity (correct key, valid timestamp, unique nonce), it performs a silent action: it instructs the system firewall to create a temporary rule that allows access to the desired port (e.g., SSH) exclusively from the client's IP address. This rule has a defined lifespan and is automatically deleted upon expiration. To the rest of the internet, the server never had an open port. This drastic reduction of the attack surface is the first and most powerful lesson of Ghostgate.
2. Silence as a Strength: Why the Best Response is No Response
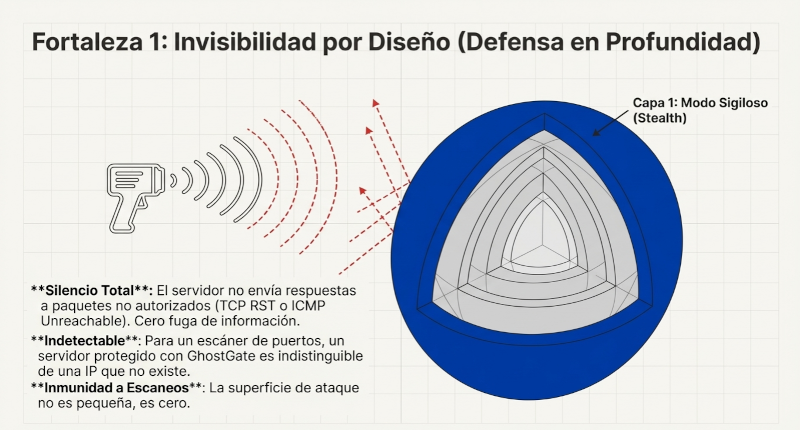
One of GhostGate's most counterintuitive and brilliant design decisions is its communication policy: the listener receiving the SPA packets never, under any circumstances, sends a UDP response. It's an information black hole.
If a packet is valid, the action (opening the port) is executed on the server, and the client simply connects to the now-available service. If the packet is invalid—whether because the key is incorrect, it's malformed, or it's an attack attempt—the listener silently discards it. There's no "error" message, no "invalid packet" message, nothing at all.
This silence is a critical security feature, based on the principle of "Zero Information Leakage." To an attacker, a server running GhostGate is indistinguishable from a "black hole" in the network or a non-existent server, thus thwarting their reconnaissance methods from the outset. By not responding, it prevents them from using techniques of fingerprinting to confirm if the service is active. Furthermore, this policy completely prevents the server from being used in DDoS amplification attacks, where a server could be tricked into sending large responses to a victim. The best response, often, is complete silence.
3. Beyond AES: A Bold Bet on Modern Cryptography
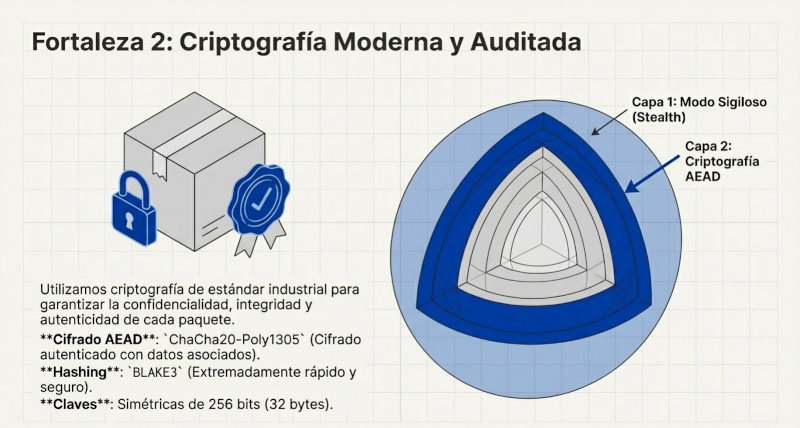
When you think of encryption, the AES (Advanced Encryption Standard) algorithm is usually the first one that comes to mind. However, the GhostGate team made a deliberate and well-considered decision not to use it. Instead, they chose ChaCha20-Poly1305 for authenticated encryption and BLAKE3 as a hashing algorithm.
This choice, far from being esoteric, aligns with cutting-edge standards like TLS 1.3 and reveals a deep understanding of practical cryptography. The advantages of ChaCha20-Poly1305 over AES-GCM are clear: higher performance on CPUs without hardware acceleration (AES-NI), superior resistance to side-channel attacks thanks to its simpler design, and a lower probability of implementation errors.
The case of BLAKE3 is a lesson in strategic foresight. Although its use in the current MVP's packet processing is minimal, it was chosen because it is an extremely fast and secure hashing algorithm, ready for future use cases such as nonce hashing, configuration integrity verification, or as a basis for key derivation functions (KDFs). This choice is not based on novelty, but on a conscious prioritization of practical performance and security over simply conforming to the most popular options.
4. Prepared for the Quantum Future (Before It Becomes a Problem)
It's remarkable to find such detailed planning for the quantum computing era in a project, even one in its MVP phase. Ghostgate not only acknowledges the future threat but also addresses it head-on in its current design.
The documentation explains the "Harvest Now, Decrypt Later" threat (Harvest Now, Decrypt LaterAn attacker captures encrypted traffic today and stores it, waiting for a future quantum computer to be able to break the encryption. Ghostgate already has an inherent advantage: by using exclusively symmetric cryptography (a shared key), it is immune to Shor's algorithm, which will annihilate the asymmetric cryptography (RSA, ECDSA) that protects much of the internet.
Symmetric cryptography is indeed affected by Grover's algorithm, which reduces the complexity of searching for a key from N possibilities to the square root of N. For a 256-bit key, this reduces the effective security to 128 bits. While still extremely strong, the project's foresight is devastating when compared to other systems. As its documentation indicates, after a quantum attack, GhostGate's security is "reduced but viable" (128 bits), while RSA/ECDSA-based systems like SSH or TLS 1.2 are left "«Completely broken»(0 bits of security). Even so, the project already has a migration plan to a hybrid mode with CRYSTALS-Kyber. This level of healthy paranoia is a masterclass in long-term security design.
5. The Impossible Fusion: Extreme Security and User-Centered Design
After discussing post-quantum cryptography and niche algorithms, one might think GhostGate is an esoteric and difficult-to-use tool. Nothing could be further from the truth. The fifth and perhaps most important lesson is its obsession with "usable security," which is a direct mitigation against the "Weak Configuration" attack vector identified in its threat model.
The most robust security is useless if it's so complex that users misconfigure it. GhostGate tackles this problem head-on with concrete examples:
• Interactive Setup Wizard (ghostgate-setup): Instead of leaving the user to navigate a configuration file, a wizard guides them, validates each entry, and issues clear warnings about unsafe options, such as performing a binding to 0.0.0.0, allowing excessive port lists (more than 100) or configuring excessively long access durations.
• Categorized error messages: If a request fails, the system provides clear errors with codes such as [AUTH_xxx], [AUTHZ_xxx] either [TIME_xxx], which help diagnose the problem without revealing internal details to a potential attacker.
• Key lifecycle management: The tool tracks the age of keys and proactively warns when a key has exceeded the recommended threshold (e.g., 90 days), promoting good security hygiene.
This philosophy is enshrined in their security guidelines: "Security mechanisms should not create friction that encourages users to circumvent them." GhostGate demonstrates that the safest path should also be the easiest.
Conclusion
GhostGate is much more than an ingenious firewall tool. It's a masterclass in a coherent and modern security philosophy. Through its design choices, it teaches us that true strength can lie in invisibility, that silence is a powerful response, that choosing the right cryptography goes beyond the most well-known names, that future-proofing is crucial, and above all, that cutting-edge security must be accessible to those who need it.
It leaves us with a fundamental question that we should all ask ourselves when designing our defenses: What if the best defense is not a higher wall, but a door that only exists for those who already have the key?
